Arm Reverse Engineering & Exploitation

Day 1: Arm (A32 & A64) Architecture Internals, Assembly, and Shellcode Development
Day 2: Static and Dynamic Analysis, and Memory Corruptions
Day 3: Exploit Development for Router Firmware with Advanced ROP Techniques
For researchers aiming to keep up with the latest technology trends, the Arm architecture has become more relevant than ever. Until recently, Arm assembly was mostly found in mobile and IoT devices. Nowadays, more and more laptops and servers are based on the Arm architecture.
Now is the perfect time to level up your skills with the most beautiful assembly language: Arm!
The first day of this course is designed to give you a deep understanding of the Arm architecture and the A32 and A64 instruction sets. Not only will you learn how to read Arm assembly, but you will also develop your own assembly code (shellcode) to deepen your understanding.
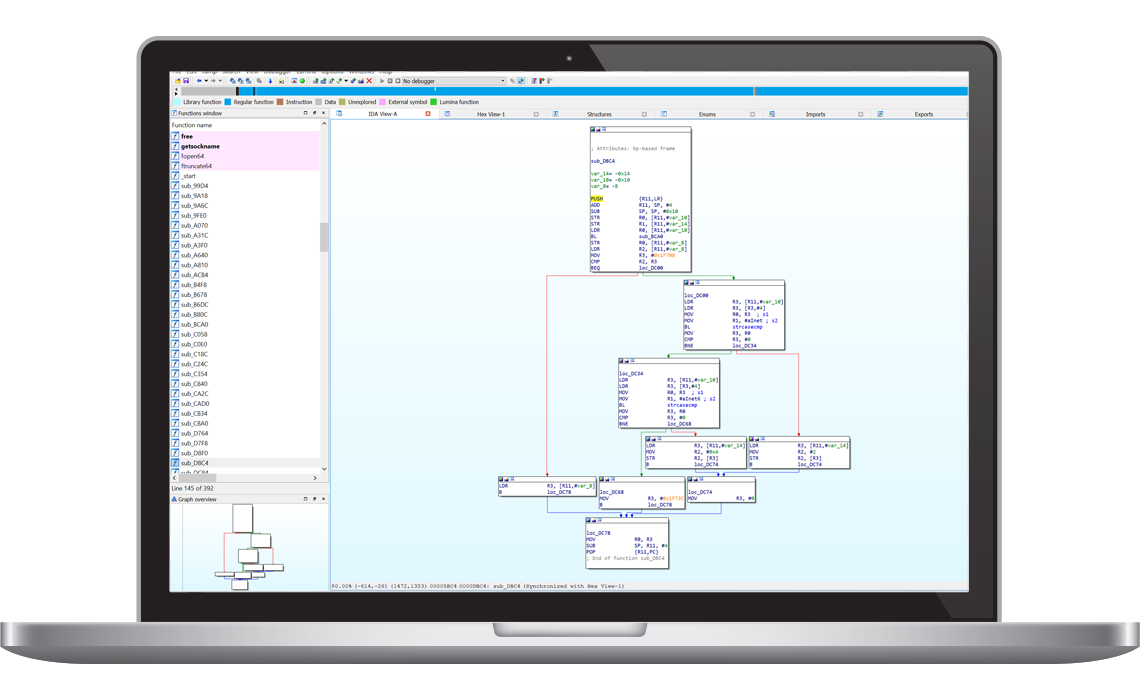
During the second day, you will use your newly acquired assembly knowledge to perform static and dynamic analysis of compiled programs, as well as debug memory corruption vulnerabilities.
Based around two real-world router firmware targets, the third day will teach you the process of building and debugging memory-corruption exploits from scratch, and develop advanced mprotect ROP chains to exploit a vulnerability in real router firmware.
Bonus content:
Learning doesn't stop after the training! On top of all the course material including slides, solution slides and scripts, and the lab workbook, attendees will receive the bonus content worth 3 extra training days for free. This includes slides, solution slides, solution exploits, and step-by-step
lab instructions (workbook):
- Format String vulnerabilities
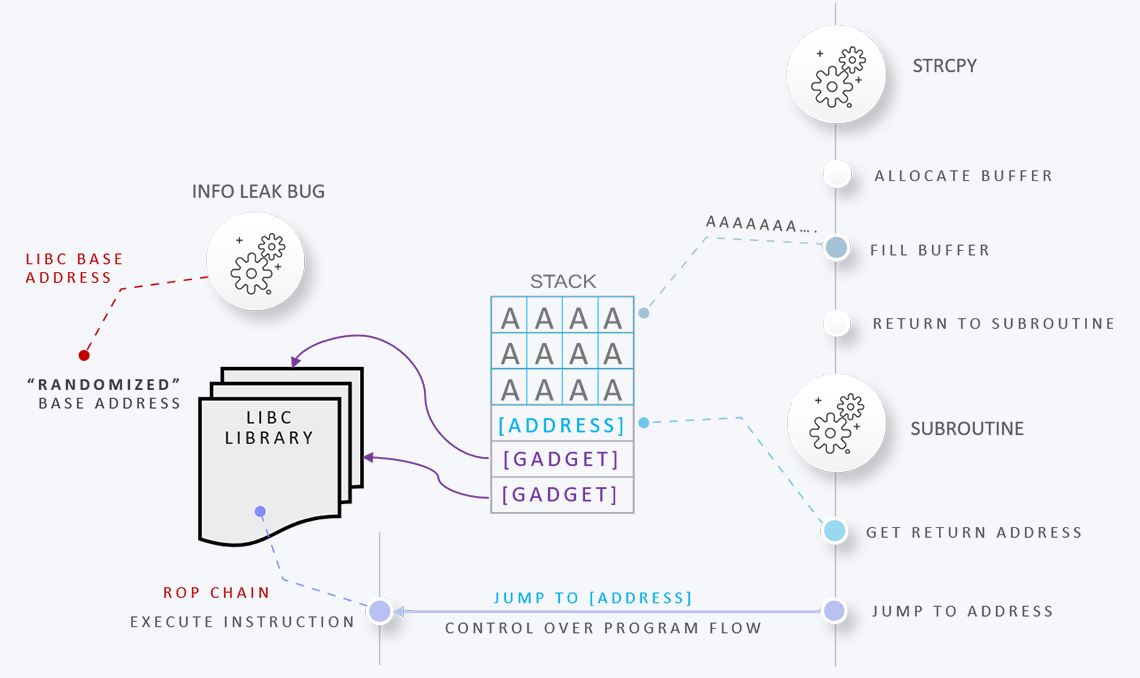
- Bypassing ASLR with information leaks
- Bypassing Stack Canaries with info leaks
- Lab: write exploit to bypass ASLR
- Lab: write exploit to bypass Stack Canaries
- Introduction to heap exploitation
- Heap layout, malloc, free, corrupting vtables
- Categories of heap vulnerabilities
- Concepts and heap exploitation techniques
- Lab: write exploit to bypass ASLR
- Lab: Use-after-free Heap Exploit
- Lab: Trigger the heap overflow
- Lab: Build a relative read exploit primitive
- Lab: Build an arbitrary read exploit primitive
- Lab: Build a complete exploit chain to bypass all on-device mitigations
Additionally, all attendees will receive free access to the upcoming online training courses for the same topics (including bonus content topics).
This course is for you if you...
... enjoy learning new skills and challenge yourself,
... are detail-oriented and not scared of assembly,
... want to expand your skill set to gain a competitive advantage in the workforce,
... don't have experience with Arm assembly but always wanted to learn it,
... have experience with other instruction sets but want add Arm to your portfolio, or
... are a macOS researcher who wants to speak the language of the M1 chip
Do I need Arm assembly knowledge to take this course?
No. Even if this is your first assembly language, you will learn it from scratch during this course. The course will start from the very beginning and work up to more advanced topics.
I already know x86/64 assembly; is this course for me?
Yes. If your focus has primarily been on other architectures, and you want to expand your skill set for the cases where you need to deal with Arm-based binaries, this course is for you.
I'm not a malware analyst / vulnerability researcher / reverse engineer, but I would like to become one. Is this course for me?
Yes. If you want to become a vulnerability researcher or malware analyst, being able to read disassembly to perform low-level analysis is a core skill requirement. Analyzing the disassembly of a vulnerable or suspicious function can help you understand under which conditions it is triggered or the precise data stream required to exploit it without crashing the program.