Course: IoT Exploitation


Learn Arm Assembly
Learn the internals of the A32 instruction set.
Analyze Vulnerabilities
Dissect and exploit memory corruption vulnerabilities.
Write Exploits
Develop and debug memory corruption exploits.
Bypass Exploit Mitigations
Learn how to bypass common exploit mitigations.
Compromise the Device
Write exploits and hack real-world router firmware.
Tired of simple buffer overflow challenges? Waste no time and get your hands on real targets. This course takes attendees from the basics of Arm assembly to debugging vulnerabilities in real router firmware. By the end of this course attendees will have written N-day exploits and bypassed on-device exploit mitigations.

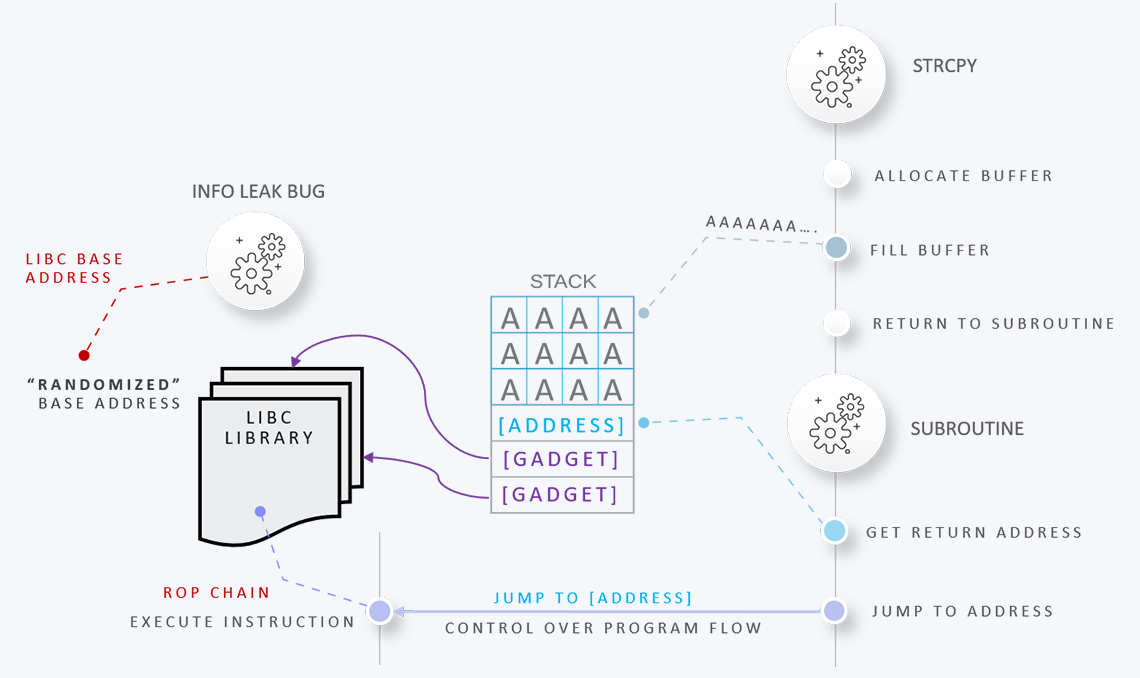
Who wants to stare at boring text slides for days? Nobody. Azeria Labs courses are designed to improve the learning experience by addressing different learning styles. Packed with aesthetically pleasing visual explanations of complex technical concepts, the course material helps ensure attendees understand and retain more knowledge and learn faster.
To keep participants engaged and on track, attendees will receive a physical workbook to guide them through each lab. This comprehensive training workbook is designed to take attendees step-by-step through every concept taught in class, reinforcing learning and making sure no step is overlooked.

Lose no time on complicated installations, managing dependencies, or troubleshooting configuration problems on software before class. Attendees get pre-configured and ready-to-use lab environments with all necessary tools, scripts, exploit templates, and emulations, in form of a VM or cloud access.
For detailed course outlines and price quotes, email contact [at] azeria-labs.com from your company email account. Please note that our private training sessions are available to corporations and government organizations with minimum class sizes of 10 people.